Security Circumstances and Multi-Layered Protection (Security Solution from T4U Part 1)
※This article is a guest post by T4U Co.,Ltd
In general, we regard ‘Security’ as a kind of obstacle that prohibits various things or makes anything inconvenient. The security solution T4U proposes enables the users to build an environment that they can concentrate on their own business. In addition to being safe, the users can spend their time in their proper work instead of managing passwords and rules.
Security incidents in Japan
The following table and chart were reported by Japan Network Security Association on May 2017 and these elements show security incidents occurred in 2016 and those causes.
As you can see, the total number of persons whose info was leaked is much larger than we assumed.
According to the report, it is about 15,100,000 persons.
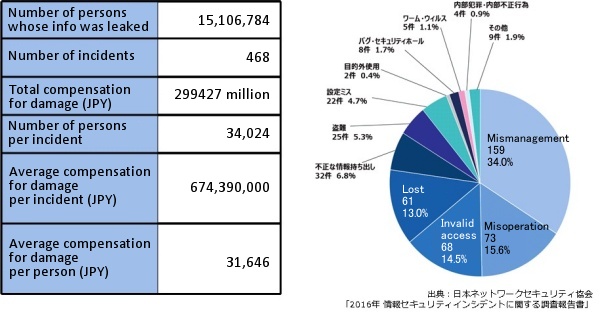
Since one popular incident by Japan Pension Service in 2015 was 1,250,000 records, you can realize how huge that number is. Actually, this incident is regarded as the reason the IPA, Information-technology Promotion Agency, proposed a multi-layered protection.
The pie chart shows various causes for information leakage. It includes many types such as human error, unauthorized access, computer virus and it is difficult to specify some specific reasons.
Thus we start thinking we need multiple protections and the security measure method ‘multi-layered protection’ is becoming popular.
Multi-Layered Protection
‘Multi-layered protection’ is a security measure method proposed by IPA in June 2015. IPA lists the following four points to be followed:
1. Decreasing the risk of computer virus infection
2. Separating terminals or servers for important work
3. Adding limitations to server for critical information
4. Preparing for reactions to something happened
Source: IPA (Japanese only)
The following diagram might be self-explanatory:
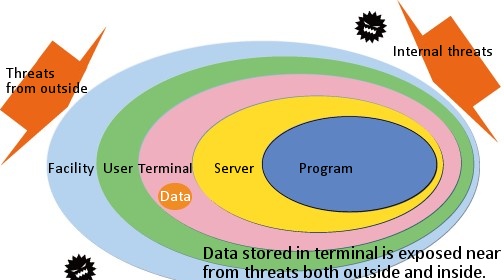
‘Data’ is one of the assets companies must protect. In order to protect that data, the measures by multi-layered protection would be effective. The following three points would be a key on managing 4 points for multi-layered protection using IT technology:
・For authentication:
Ensuring that only authenticated user can access the data.
・For external device:
Ensuring that only permitted device can access the system.
・For data:
Monitoring and managing the data thoroughly in a protected environment.
The VIP system, a solution provided by T4U works as follows:
 For Authentication For Authentication・User Authentication ・Device Certification | 
| Vein Authentication Device |
 For Device For Device・OS Management ・Application Management | 
| Thin Client Terminal |
 For Data For Data・Archiving and Encryption in a Protected Server ・System Monitoring | 
| Log Management System Realtime Monitor |
※For details about VIP system, please refer to: What is VIP, Vein Identification Platform (Japanese only)
・Secure identity verification by vein recognition
・Thin client terminal prevents information leakage
・Detailed access control options
・Working together with automatic encryption software
・Recording a complete log
Author of this article

| T4U Co.,Ltd |